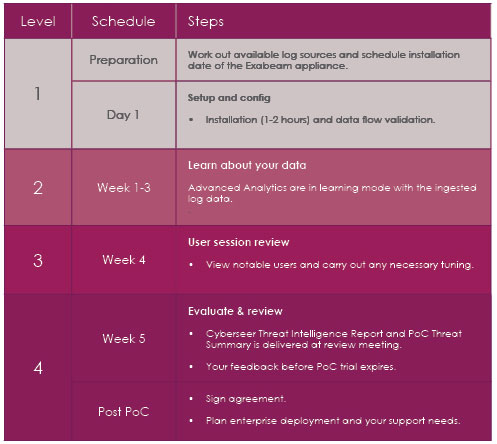
What is an Exabeam Proof of Concept?
A Proof of Concept (PoC) is a trial that allows you to evaluate the leading security intelligence platform Exabeam within your own environment using your data to prove the value of the technology.
The PoC also allows organisations to understand why world leading companies are relying on Cyberseer’s managed service to detect damaging threats.