In response to a tide of interest in our technology solution Darktrace, we have compiled the following list of “Frequently Asked Questions” (Darktace FAQs) and their answers, which we hope will help broaden your knowledge.
We are particularly pleased to see a wide variety of questions being asked of Cyberseer’s Threat Analysts who are recognised for their expert capabilities in research, monitoring and in-depth investigations. They use insight from Darktrace’s ‘Enterprise Immune System’ approach to provide comprehensive support for our customers and combat targeted threats.
To help you find the answers you are looking for more easily, we have listed the questions here. Just click on the question and it will take you to the answer. If your question isn’t listed, please send it to our Threat Analysts team or schedule a call.
If you already have Darktrace and are interested in maximising your investment, Cyberseer is offering Free Darktrace Health Assessments for a limited time. Schedule Your Assessment Today!
- What is Darktrace?
- Is Darktrace a SaaS company?
- What is Darktrace used for? How does Darktrace work?
- Where can I put Darktrace?
- How does Darktrace work?
- What data can Darktrace ingest?
- Can Darktrace deploy end user agents?
- How much resource do I need to run Darktrace?
- What is Cyberseer’s SOC Service for Darktrace?
- Is my data sent anywhere else?
- Where is Darktrace hosted?
- What does Darktrace integrate with?
- Is the Darktrace Platform easy to scale?
- But, what is the threat visualiser?
- But what benefits do Darktrace and the Threat Visualiser offer?
- What type of anomalies does Darktrace detect?
- What if I get an infection before we start? What if my network is already compromised?
- Can Darktrace derive value from encrypted network traffic?
- Can Darktrace support and interact with virtualised environments and cloud services?
- What is the difference between Darktrace Detect, Darktrace Prevent, Darktrace Respond and Darktrace Email?
- What is the Darktrace cSensor (Darktrace DETECT & RESPOND/Endpoint)?
- How do you manage response times within Darktrace?
- How does Darktrace monitor specific SaaS apps for detection and response?
- What are the Darktrace models and how do they work?
- What are the Darktrace models capable of detecting?
- Why is this effective?
- What are the Darktrace model breaches?
- What are the Darktrace metamodels and their use?
- What is Darktrace Advanced Search?
- How does Darktrace identify hostnames?
- How does Darktrace identify OS Type?
- How does Darktrace Email prevent phishing?
- How can you search within Darktrace Email?
- Within Darktrace Email, how can you release and hold emails or links?
- What are the models with Darktrace Email?
- How does Darktrace Email differ from traditional Darktrace?
- Is Darktrace a SIEM solution?
- Why is Darktrace different?
- What is the Cyberseer SOC monitoring process using Darktrace?
Have More Questions?
Contact us today
SOC Services for Darktrace
What is Darktrace?
Darktrace is a suite of AI-powered tools that deploy machine learning models to identify and tackle cyber attacks in real-time. The varying products monitor network and email for active threats. All these systems can be interconnected and work by learning the patterns of a network to detect any anomalies for investigation by a security team.Is Darktrace a SaaS company?
Darktrace offers both SaaS & on-premises deployments. The additions of the SaaS master console and SaaS connectors have added tremendous flexibility to Cyberseer. Cyberseer would work in partnership with your aligned representatives from Darktrace to best meet technical, commercial and resource objectives for your deployment.What is Darktrace used for? How does Darktrace work?
Darktrace is an advanced threat detection solution that utilises machine learning models to detect anomalous behaviour in the network telemetry or logs ingested into the platform.Where can I put Darktrace?
The Darktrace System is delivered as a single appliance that takes up 2U of rack space and can be installed, configured and tested in less than three hours. All user interfaces are accessed by a web browser, including the 3D Threat Visualizer and a management portal.How does Darktrace work?
Darktrace is an advanced threat detection solution that utilises machine learning models to detect anomalous behaviour in the network telemetry or logs ingested into the platform.What data can Darktrace ingest?
Dakrtrace virtually accepts every data format and typically works with core internal network traffic, collected by one of the following methods:- Port spanning the organisation’s existing network equipment.
- Inserting or re-using an in-line network tap.
- Accessing any existing repositories of network data.
Can Darktrace deploy end user agents?
Yes, although it isn’t mandatory for the deployment of Darktrace. Darktrace has an agent called the C-Sensor which is designed to pull the network telemetry from devices that can’t be captured by network traffic from a core switch.How much resource do I need to run Darktrace?
The Darktrace platform can easily be integrated into your existing detection and incident response processes as an additional, high-integrity source of alerting. Alternatively, we can do it for you. Cyberseer’s threat detection and analysis managed security service turns insight into actionable intelligence.What is Cyberseer’s SOC Service for Darktrace?
Cyberseer offers SOC Services for Darktrace which leverages expert human analysis to provide real-time, accurate and actionable intelligence about threats identified in the enterprise environment. Cyberseer’s Analysts are experts in defence, intelligence and interpreting suspicious activities around probable threats and recommending mitigation’s appropriate and suitable for you. This process includes analysing traffic entering, leaving and inside the enterprise network. Threat analysis of this kind is often like finding a needle in a haystack and requires skills and understanding far beyond the normal abilities of most security professionals. No automated technology can achieve the accuracy and insight achieved by expert threat analysts depth of knowledge and understanding. Our manual threat intelligence service involves analysing the results from behavioural modelling technology and proactively investigate the severity of anomalies that may be indicative of threat. For every incident detected, our analysts draw on their expertise, external sources of intelligence and the context of the network before presenting an informed and considered explanation of the threats faced. Investigative work is collated into a comprehensive threat report of discovered threats classified and scored in terms of severity and confidence, in conjunction with recommended actions.SOC Services for Darktrace
Is my data sent anywhere else?
All data is processed by Darktrace’s platform, and all outputs remain within an organisation’s data centre. No data is ever sent to the cloud or shared with a wider user community outside of Cyberseer’s Analyst department. A VPN connection installation is recommended to enable full support from Darktrace’s Cyber Security Specialists.
Should you wish to not progress beyond the Proof of Concept (PoC) stage, all data is securely destroyed and removed from discs on completion of the PoC.
Where is Darktrace hosted?
Darktrace is hosted in Microsoft Azure.
What does Darktrace integrate with?
Darktrace has a vast number of integrations into SaaS applications and security tools. Darktrace has a full list available on request.
Is the Darktrace Platform easy to scale?
A single Darktrace appliance can take multiple inputs of network traffic and cover up to tens of thousands of individual machines, depending on peak traffic volumes. Multiple Darktrace appliances can cluster to cover geographically distributed networks, without the need to move large volumes of data around your network.
The Darktrace appliance is sized on throughput in gigabytes, and it scales linearly.
With the incorporation of SaaS, Darktrace’s scalability is further optimised, allowing organisations to easily adapt and expand their cybersecurity capabilities in response to evolving threats and changing network requirements.
But, what is the threat visualiser?
The Darktrace Enterprise Immune System is complemented by the Threat Visualiser, a graphical and interactive 3D interface designed to specifically enable analysts to visualise behaviours and investigate anomalies. The Threat Visualiser provides a real-time operational indication of the threat level an organisation faces at any given time.
These visual insights provide the organisation’s Threat Analysts or the Cyberseer forensic team with a representation of the data flows across the business network historically and in real-time, both external and internal and between all machines and users. The Threat Visualiser is a high-level interface that can be used by Threat Analysts with minimal training.
Using Bayesian algorithms, it identifies top threats that are genuinely anomalous, allowing organisations to focus their attention and expertise proportionately, on areas of considerable risk.
Should an anomaly emerge, the Threat Visualiser will show the events leading up to and during the anomaly and contextually expose the factors that are considered out of the ordinary.
But what benefits do Darktrace and the Threat Visualiser offer?
- A single worldwide view of the enterprise.
- Flexible dashboard.
- Learns on the job & understands your entire business.
- Designed for Threat Analysts.
- Global threat monitoring in real-time using sophisticated self-learning mathematics.
- Signature-free mathematical approaches allow the detection of new emerging attacks that have not been seen before.
- Capability to replay historical data and fight back in real-time.
- Manually create rules and heuristics.
- Network appliance plugs directly into infrastructure and installs in one hour.
The Darktrace Threat Visualiser allows the corporate policy to be enforced and users can be monitored in accordance with defined criteria. The Threat Visualiser is powered by the Darktrace Platform and helps organisations to identify key assets and intellectual property. It allows threat levels to be monitored as they evolve and enable preventative actions to be made to protect an organisation and ultimately interrupt the cyber kill chain.
What type of anomalies does Darktrace detect?
The range of anomalies Darktrace detects is very broad, because it sits at the heart of an organisation’s network. Darktrace finds anomalies that bypass other security tools, due to its unique ability to detect threats without relying on rules, signatures or any prior knowledge of what it is looking for.
The variety of anomalies is vast because the principle of the software is that it has visibility of all the traffic as it flows inside and outside the organisation.
This allows us to see compliance issues, poor configuration, management/housekeeping and malicious attacks without signatures. Darktrace is not constrained by pre-defined categories of threat types or malware families – Darktrace can detect anything from ransomware to bitcoin mining, to Advanced Persistent Threats, and more.
What if I get an infection before we start? What if my network is already compromised?
Perfect data is not needed. Darktrace leverages two different approaches to detecting anomalies: comparing each device’s behaviour to its own history and comparing devices to their peers. This peer comparison allows us to avoid learning existing bad behaviour as normal because compromised devices will exhibit behaviour different from their immediate peers.
So if your network was compromised before work commenced, a pre-existing intrusion would be discovered as anomalous in comparison to the normal behaviour of similar devices.
Can Darktrace derive value from encrypted network traffic?
Encrypted traffic, regardless of whether it is decrypted within Darktrace, provides very valuable information. The time of day, source, destination, size of the transfer, and even the existence of encrypted data are all available without decryption. This traffic is considered ‘information-rich’.
Encrypted data is a normal part of enterprise networks and Darktrace will operate successfully ‘out of the box’ without the customer needing to decrypt SSL/SSH communications or provide private keys.
Can Darktrace support and interact with virtualised environments and cloud services?
Yes, Darktrace’s vSensor allows you to extend visibility into your virtual environment to include this traffic between virtual devices. The vSensor installs into the hardware server as another virtual machine. Once configured with the VM manager and provided with network traffic, the vSensor spans traffic from a virtual switch and will send data to the master Darktrace appliance.
The vSensor can only be used in conjunction with a physical Darktrace appliance. If it is not possible to span a virtual switch, the vSensor also supports the ingestion of traffic from multiple OS-Sensors. The OS-Sensor is installed on each virtual device that is to be monitored, and it captures all of the network traffic to/from that device, sending it to the vSensor for analysis.
The vSensor plus OS-Sensor setup is suitable for cloud infrastructure like AWS, where you may not be able to span from a virtual switch. The OS-Sensor provides network visibility of the devices it is installed on.
What is the difference between Darktrace Detect, Darktrace Respond, Darktrace Prevent and Darktrace Email?
Darktrace Detect – formerly Darktrace’s flagship AI cyber defence solution, the enterprise immune system. It combines real-time threat detection, network visualisation and advanced investigation capabilities in a single unified system that is fast and easy to install. Darktrace Detect provides visibility and detection into, on-premise, IaaS, SaaS, IoT & ICS.
Darktrace Industrial is a part of Darktrace Detect and provides cyber defence AI technology that is specifically developed to detect cyber threats and latent vulnerabilities in both OT environments, such as SCADA systems and IT networks.
Darktrace Response – Formerly Antigena, powered by Darktrace’s multi-award-winning AI. Darktrace Response is an autonomous response solution that takes surgical action against in-progress cyber threats, limiting damage and stopping their spread in real-time.
Darktrace Prevent – Two modules make up Darktrace Prevent. Attack Surface Management (ASM) and End-2-End.
ASM – uses AI to understand what makes an external asset yours, searching beyond known servers, networks, and IPs, typically surfacing 30% – 50% more assets than an organisation realises it has.
End-2-End – Proactively prevents cyber-attacks before they occur. Identifies and prioritises high-value targets and pathways to secure vital internal systems and assets. Augment your pen-test strategy with real-time attack path modelling.
Darktrace Email – Formerly Antigena Email, forms a key component of Darktrace Detect and Response by integrating into the enterprise inbox. This module of the Darktrace platform uses AI to learn your ‘normal’ pattern of life for the inbox to provide an extra layer of defence to email threat vectors.
What is the Darktrace cSensor (Darktrace DETECT & RESPOND/Endpoint)?
Darktrace DETECT & RESPOND/Endpoint extends the visibility of the Darktrace Cyber AI Platform and the reach of Darktrace RESPOND autonomous response to remote devices. Coverage is provided via Darktrace Client Sensor (“cSensor”) agents installed directly on the endpoint to monitor and control network activity. Unlike the osSensor, it requires no connected vSensor and performs data analysis on-agent.
The cSensor is designed to extend coverage, visibility and Darktrace RESPOND autonomous response over a dynamic workforce. Deployment in virtualised networks is not the primary deployment scenario. It is ideally used in combination with other Darktrace virtual sensors and deployment options to achieve a combination of greater and simpler visibility.
How do you manage response times within Darktrace?
For some use cases such as ransomware, we find Darktrace Autonomous Response decision-making is perfect for acting quickly and responding to those disruptive and sophisticated cyber-attacks. Other use cases require human expertise and contextual analysis. Context allows our Analysts to understand the threats and trends that may not instantly affect your organisation and do not require an immediate response taking place. Cyberseer’s SOC works closely with customers to gain an in-depth understanding of their environment and organisation, thus understanding the true context of a threat in your environment. View more information on SOC Services for Darktrace.
How does Darktrace monitor specific SaaS apps for detection and response?
Darktrace can protect the hybrid workforce from attacks that evade static and siloed defences, such as insider threats, compromised credentials, and accidental data loss. Darktrace can easily adapt through self-learning AI to monitor corporate cloud accounts and collaboration tools as organisations evolve. Within minutes you can be notified of account breaches and stop attacks, all whilst your business continues to operate as usual.
What are the Darktrace models and how do they work?
Darktrace operates on an intelligent system of Models, which can be simplified as sets of criteria designed to trigger a “breach”. Within your Darktrace console, there are over 1000 distinct models, each serving a unique purpose. Some of these models were developed by Darktrace and tuned to your environment by Cyberseer – whilst others are exclusively developed by Cyberseer.
Pastebin and other equivalent sites are a popular method of exfiltrating data. Let’s investigate how the Pastebin detection model within your environment works to illustrate model logic. This model triggers a breach based on several different criteria. The first of these criteria is if the message field contains the phrase “PasteBin connection” and if the rarity score reaches 95 or more. The rarity score is designed to adjust the model to the average behaviours of your environment, as it will lower with more frequent visits to PasteBin. This is designed to tune out any possible BAU PasteBin activity.
The second set of criteria assesses if the connection is outgoing, reaches a rarity score of 95 or higher, and is going to a destination hostname containing keywords like PasteBin, GhostBin, TextBin and their equivalents. When these conditions are met, a model breach is triggered – leading to the appearance of the activity in the tray within the Darktrace console. This breach serves as an alert to prompt further investigation by an analyst into this activity.
What are the Darktrace models capable of detecting?
The range of anomalies Darktrace detects is very broad because it sits at the heart of an organisation’s network. Darktrace finds anomalies that bypass other security tools, due to its unique ability to detect threats without relying on rules, signatures, or any prior knowledge of what it is looking for. The variety of anomalies is vast because the principle of the software is that it has visibility of all the traffic as it flows inside and outside the organisation. This allows us to see compliance issues, poor configuration, management/housekeeping and malicious attacks without signatures. Darktrace is not constrained by pre-defined categories of threat types or malware families – Darktrace can detect anything from ransomware to bitcoin mining, to Advanced Persistent Threats, and more.
Why is this effective?
The system of models Darktrace chooses to operate with is renowned for its ability to learn the intricacies of your environment. This doesn’t only mean that Darktrace can tune out behaviour that would be deemed suspicious in another environment but is BAU for your environment – it also means that general anomalies can be detected without relying on signatures.
A signature-free method of anomaly identification provides a substantially increased insight into anomalous behaviour across the network – and therefore increased control over security.
With the correct licensing, you may also have access to autonomous response. Autonomous response allows quick response to certain actions to be set up, and this will be carried out without human input. This feature can completely eradicate the threat that the need for human investigation creates – as a device can be completely blocked from all network connections until the activity is deemed to be benign.
What are the Darktrace model breaches?
Breaches are simply an activity that occurs that warrants investigation. As mentioned, Darktrace models are designed to pick up on different types of activity within the network that are deemed anomalous enough for investigation. A model “breaches” when that activity is picked up on and the breach is placed into the Darktrace console for investigation by an analyst.
For ease of use, direct links to model breaches can be sent – simply append ‘/#modelbreach/10740’ to the end of the URL, the number after #modelbreach/ is the breach ID.
What are the Darktrace metamodels and their use?
Metamodels operate similarly to traditional models, however, the criteria that trigger a breach is the breaching of another (or several other) models. Metamodels can be very useful for identifying a broad picture of activity within the environment and for the prioritisation of investigative resources. Some of the most triggered metamodels include:
- Lots of model breaches were seen.
- Multiple devices triggering the same model breach.
- Multiple lateral movement model breaches are seen.
Bespoke metamodels can also be developed by Cyberseer, as these will allow for further insight into the potential threats within your environment you view as top priority. For example, a metamodel has been developed in the past to identify file storage use along with anomalous login locations.
What is Darktrace Advanced Search?
Advanced search is a feature of Darktrace that allows an analyst to perform an in-depth investigation of raw logs. This feature can also provide a useful UI to perform statistical analysis.
When the event log of a breach is viewed, this will only provide an analyst with the activity that triggered that specific anomaly. To access advanced search, the triangle button next to the activity should be clicked – and the below series of options should appear.
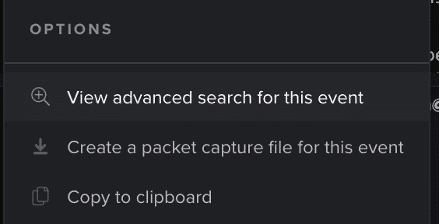
Advanced search will then present the user with the raw log for the specific event the user pivoted to the advanced search window on.
If this log is expanded, each field can be filtered on to expand the query and gain more insight into the activity. The quick query-building filters are seen in the screenshot below.

One of the most day-to-day uses of Darktrace advanced search is to verify if MFA was used on a login. The first step for this would be to pivot into an advanced search from the breach – and then be presented with the relevant raw log. There are several different ways MFA can be verified, which would need further investigation. However, in the case we’re looking into MFA was satisfied by the claim in the token.
How does Darktrace identify hostnames?
Darktrace identifies the hostname of devices from DHCP or Kerberos traffic. This can be configured to the preferred method of identification for specific subnets.
<Insert Example for DHCP>
Example for Kerberos
01/15 06:19:46 kerberos
1484461186.3829 CpAhXb1u0vLJYwDq00 192.168.253.055 52085 192.168.253.42 88 – – AS: Password incorrect false CSLT00010 CYBERSEER.LOCAL Administrator krbtgt
How does Darktrace identify OS Type?
The operating system is detected by TCP settings and flags which vary between OS versions. For example, windows act differently to OSX as it sets different window size scaling settings on the initial TCP handshake. We have deployed a database of OS fingerprints onto the product which performs this assessment.
How does Darktrace Email prevent phishing?
Darktrace Email is a self-learning AI solution for the inbox, which operates by learning the normal ‘pattern of life’ for every user and correspondent. The technology builds an evolving understanding of the ‘human’ within e-mail communications. By treating recipients as dynamic individuals and peers, Darktrace Email uniquely spots subtle deviations from ‘the norm’ that reveal seemingly benign e-mails to be unmistakably malicious.
Darktrace Email can also stop a full range of attacks including social engineering and impersonation, business e-mail compromise, supply chain account takeover, external data loss and novel unknown malware.
How can you search with Darktrace Email?
When accessing the homepage of the Darktrace Email console, the below search bar is seen at the top of the page.
Clicking into this search bar will present the following filtration options.

From, To and Subject tend to be the easiest methods of narrowing down a search query to identify a phishing campaign or broader set of emails within your environment. However, if searching for a specific email it is faster to search by the email ID if that is available to you.
This UUID can be copied from the specific email it is attributed to, by clicking the hamburger menu when investigating the email.
Within Darktrace Email, how can you release and hold emails or links?
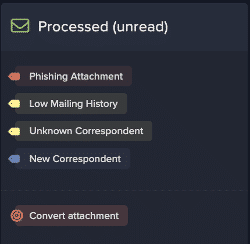
Two of the most used protections within Darktrace Email are holding emails and locking/totally blocking links. When an email is held, the investigative details on the email will show the anomalies that led to the email being held – for the message seen in the screenshot below, it was held due to having a potential phishing attachment.
If this email needs to be released, this feature can be accessed via the hamburger menu within the investigative screen.
With regards to emails that have contained locked links that have been investigated and found to be benign – the process is the same. The user will not be able to access the link from the original email, as the actions are tied to that specific email. Releasing the email will send a new copy to the user’s inbox, allowing them to access any previously locked links.
What are the models with Darktrace Email?
Darktrace Email operates on the same foundation as the more traditional Darktrace console – via models. These models “breach” in the same way – when certain, specified criteria are met.
An important note to make on this criteria specification is that the content of the email body cannot be involved in a model, as this data is not processed in and of itself. One example of this is that a model cannot be created to breach when a certain string is present in the email body – but a model can be created to trigger when a certain string is in the email subject.
These models can be configured to result in a wide range of possible actions:
- Adding warning banners.
- Using regular expressions to alter content.
- Stripping attachments.
- Locking/entirely blocking links.
- Holding the email entirely.
The bespoke nature of these actions allows you to handle threats to your environment in whatever way is required. For example, when a link is locked a user can still request access, providing that extra layer of security but also ensuring the user can still access the site if the link is deemed benign.
How does Darktrace Email differ from traditional Darktrace?
Darktrace Email operates off models in the same way as the more traditional Darktrace console – however, these models are now focused on email threats. Darktrace Email allows you to hold emails, notify users when messages triggering certain criteria have been sent and perform various other actions based on the models that have been developed for the environment.
Is Darktrace a SIEM solution?
Darktrace is not a traditional Security Information and Event Management (SIEM) solution. While SIEM systems focus on collecting, analysing, and correlating log data from various sources within an organisation’s IT infrastructure to identify and respond to security incidents, Darktrace takes a different approach.
Darktrace uses a self-learning artificial intelligence (AI) system, known as the Enterprise Immune System, to detect and respond to cyber threats. It employs machine learning algorithms to understand the normal behaviour of an organisation’s network and then identifies anomalies or deviations from that baseline. Unlike SIEM solutions that rely on predefined rules and signatures, Darktrace’s AI adapts to new and emerging threats without prior knowledge.
Darktrace’s technology is designed to provide real-time threat detection and autonomous response capabilities, going beyond the retrospective analysis and alerting features typically associated with SIEM solutions. While both Darktrace and SIEM solutions contribute to cybersecurity, they operate with different methodologies and strengths. Some organisations may choose to use Darktrace in conjunction with a SIEM solution to enhance their overall security posture.
Why is Darktrace different?
Unlike other platforms, Darktrace learns on the job, creating bespoke protection for your organisation. By understanding the ‘DNA’ of your organisation it enables early threat detection, complementing your existing investments, significantly reducing overall risk, and leaving attackers with nowhere to hide.
Traditional tools rely on historical attack lists, while Darktrace learns about your organisation by observing user, device, and application behaviour, continuously adapting to new evidence. Darktrace Antigena can interrupt attacks within seconds. This capability is crucial for incident responders facing time pressures during fast-moving or out-of-hours attacks.
Darktrace’s standout features include:
- Self-Learning AI: Adapts like the human immune system, continuously evolving to detect anomalies.
- Anomaly Detection: Identifies threats by learning the normal behaviour of your network and detecting subtle deviations.
- Autonomous Response: Not only detects but autonomously responds to threats in real-time, minimising the need for human intervention.
- Enterprise-Wide Visibility: Offers comprehensive visibility across all digital infrastructure, including cloud environments, IoT devices, and traditional networks.
- Adaptability to Emerging Threats: The self-learning AI adapts to new and emerging threats, providing proactive defence.
- No Predefined Assumptions: It doesn’t rely on predefined assumptions, making it effective against both known and unknown threats.
- Continuous Monitoring: Operates in real-time, ensuring swift identification and response to potential security incidents.
In summary, Darktrace’s combination of advanced AI, autonomous response capabilities, and a human-centric design makes it a dynamic and effective cybersecurity solution for the ever-evolving threat landscape.
What is the Cyberseer SOC monitoring process using Darktrace?
To provide some insight into the investigative process taken, here is the typical practice for investigating one type of model breach. However, please note that this is a non-exhaustive list of steps, and these steps would need to be tailored based on the content seen in the breach.
- Identify the model breach using the threat visualiser at the bottom of the tray, some of which are seen below:
- Expanded Network Scan
- Network Scan
- ICMP Scan
- Mass port Scan
- Mysql Scan
2. The next step would be to review the model breach event logs to determine the following:
- What ports is the source device connecting to? Are they common or uncommon?
- Are the connections successful or failures?
- Are the user agents associated with tools that are related to vulnerability scanning?
- What devices is the source device connecting to? How does it compare to previous history?
- Number of connected devices? How does it compare to previous history?
3. We use the device summary to determine the following:
- Associated models that have breached within the last 7 days
g. (if any of the models below have breached, use a model-specific process): - Attack Recon tools (Kali, Nessus and OpenVas)
- Brute forcing models (Kerberos, SMB etc)
- Internal / External Data Transfer
- Enumeration Models
- New User Agent
- What is the age of the device?
- What tags does the device have appended to it?
(Security tool, Domain controller etc) - Use the advanced search to determine the following: (AS queries will vary depending on the unique breach types for the device, reference to the model breach process.)
- How many connections were made?
- Associated models that have breached within the last 7 days
4. Is the activity indicating the following behaviour:
- Host/Service Discovery
- If this is scanning services, do the logs indicate vulnerability scanning?
- If there are any external connections indicating file download, beaconing, C2 activity or data exfiltration? (Use external threat intelligence according to the activity type)
- Are you able to determine when the activity started?
Based on the information that has been collected, the analyst will then proceed to identify what caused the behaviour and classify the threat. If the threat is identified as a positive detection, standard escalation procedures are followed. If not, the breached model will be raised for tuning internally.